Software program both is or will likely be weak. It’s uncommon that you simply gained’t must replace out-of-date, unsupported or end-of-life software program. In case your job description includes software program or IT asset administration (SAM/ITAM), that is a part of your day-to-day and nothing notably out of the odd. Then add onto these updates the truth that hackers are repeatedly searching for holes in your software program to slide in a malicious assault. That is when your day-to-day will get a bit extra attention-grabbing and, in some instances, extra regarding.
If vulnerabilities are simply part of proudly owning and deploying software program, why ought to they be regarding after we know we are able to remediate?
Vulnerabilities can value organizations tens of millions of {dollars} per breach. Each time a vulnerability is exploited, it exposes precious knowledge—assume Equifax in 2017 or Capital One in 2019—and that not solely results in costly remediation, however consists of prices to these whose knowledge has been affected (the consumer and private knowledge, for instance, shared for malicious functions).
Many organizations perceive, within the basic sense, that vulnerability consciousness is essential to avoiding these expensive breaches. However in follow, numerous companies nonetheless don’t have construction and protocols in place to scale back and remediate vulnerabilities that may and can have an effect on their group. A niche nonetheless stays between detection and remediation. This offers hackers greater than sufficient time to reap the benefits of holes in your IT group.
Shouldn’t our safety group be on prime of this?
Sure. And in some instances they’re proper on prime of those that have an effect on your group. The issue is that there are greater than 13,000 vulnerabilities Flexera has detected with distributors and merchandise current in our clients’ environments. Metaphorically talking, that’s loads of home windows for hackers to climb by means of and steal valuables.
With so many vulnerabilities on the market, even one of the best safety groups have to prioritize. In these instances, groups are sometimes specializing in the extremely crucial merchandise and their vulnerabilities which might be integral to their group—the mainstay functions that can’t afford the chance or are used so extensively that the impact can be disastrous.
However safety can’t catch every part.
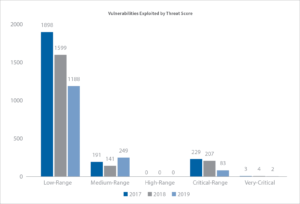
Within the newest Flexera Vulnerability Evaluation 2020 report, it was discovered that almost all of vulnerabilities uncovered had low-range risk scores—Flexera’s personal scoring of these really being exploited within the wild—and that many applications miss these exploits when specializing in extremely to extraordinarily crucial risk scoring.
What can ITAM/SAM do about this if it’s a safety challenge?
Greater than you’d assume—ITAM, and by extension SAM, are answerable for realizing the property the group deploys. It goes a step additional in that these initiatives now have safety knowledge proper alongside their asset knowledge to know the place a vulnerability is perhaps situated.
Info Safety (InfoSec) content material brings collectively data that each ITAM and safety operations discover essential to root out these exposures, together with advisory content material and risk scoring, from Flexera’s Secunia Analysis group.
With knowledge from probably the most dependable useful resource, delivering the world’s greatest software program vulnerability intelligence, ITAM professionals and groups have the capability to now assess their IT property towards not solely knowledge from the Nationwide Vulnerability Database (NVD), however the deep particulars and consistency of a trusted vulnerability ranking constructed into advisories assigned and outlined by Secunia.
Software program Vulnerability Administration
The way in which to beat software program vulnerabilities is to remain forward of them. Addressing home windows of threat is crucial for decreasing the percentages of assaults and staying safe.
OK, I understand how weak my property are. What do I do with this newfound energy?
Now’s the prospect to work along with your overwhelmed safety group and allow them to know you’ve bought their again. Whether or not you discover the mixture dataset and drill right down to particular gadgets for motion, or pull down your complete dataset to construct an evaluation (or combine elsewhere), work with them on to make recognized the place they need to hold an eye fixed—and presumably remediate ASAP.
Secunia Analysis safety advisories ship dependable, curated and actionable vulnerability intelligence. Put that knowledge to make use of and share it along with your colleagues.



